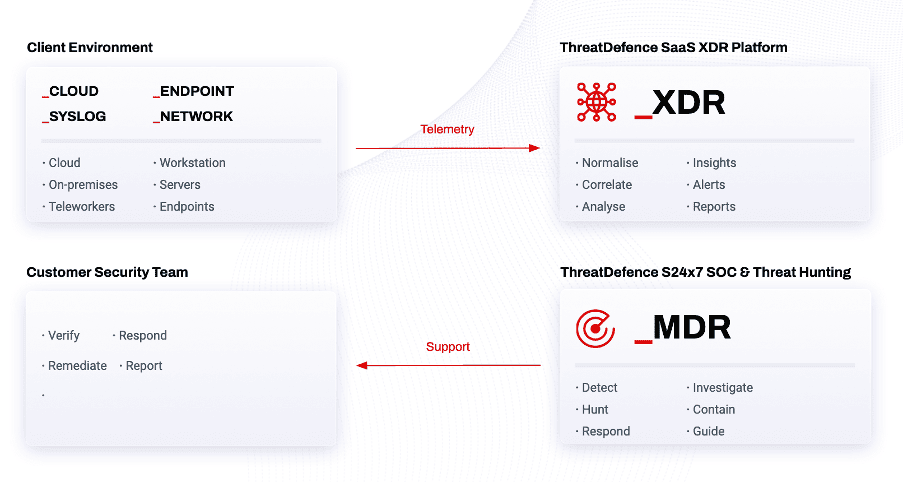
As an Australian cyber security vendor, ThreatDefence has created an easy-to-implement solution focused on the needs of Australian organisations. Our XDR platform will enable you to enhance your cyber security detection and response capabilities without conducting expensive staff training or investing in long-term implementation projects.
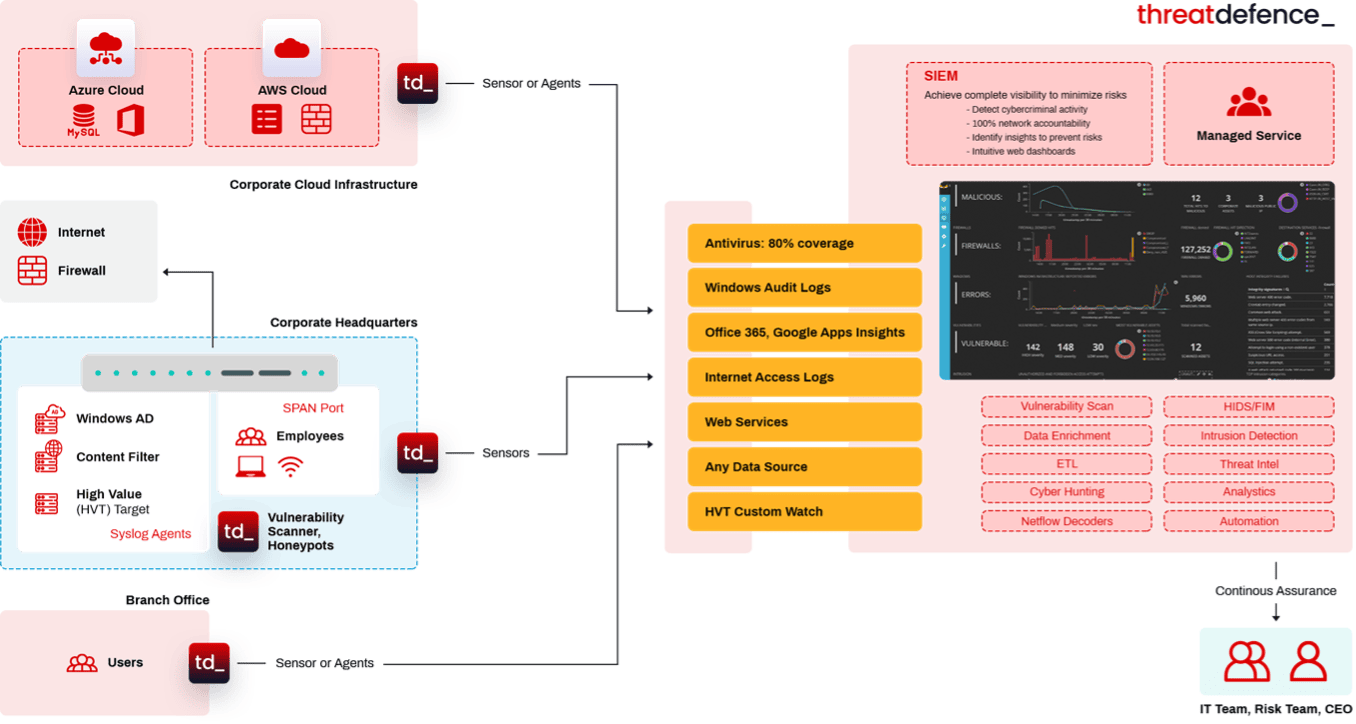
While most security solutions try to solve the threat detection problem from a particular angle, implementing detection capabilities either at the network, cloud, endpoint, or perimeter level, our platform embraces all your security data, from any environment: cloud, SaaS, network, on-premises, remote, or virtual.
ThreatDefence provides a fully managed, plug & play experience, transforming machine data into actionable insights and executive-friendly reports. You do not need to maintain multiple security tools and run complex investigations with endless cross-system integrations, as ThreatDefence establishes context for all security events in your organisation, automatically correlating data from multiple sources.
How it works
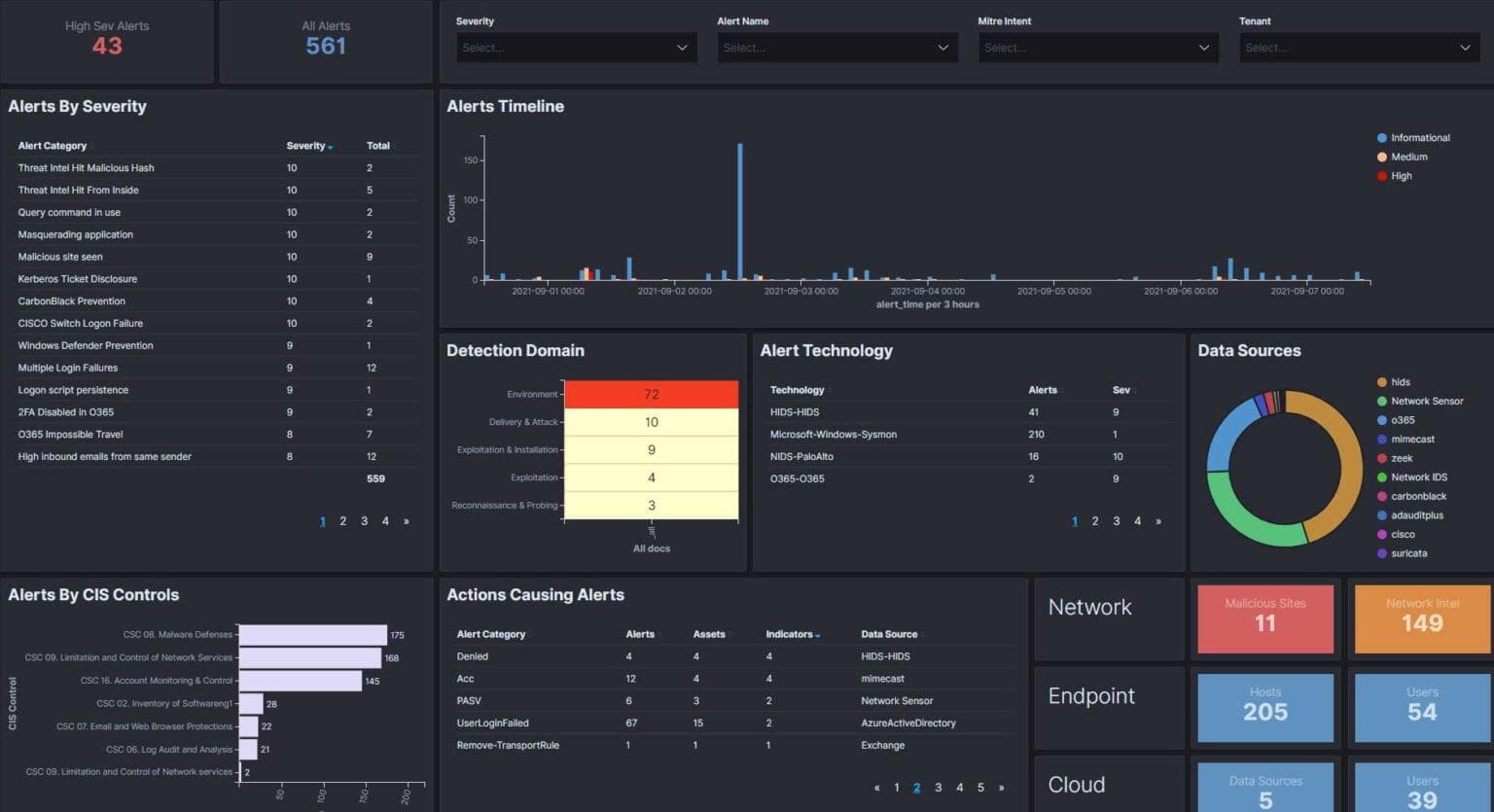
It takes minutes to deploy our cloud, network and endpoint sensors which will feed your security data into our cloud platform hosted in Sydney. We offer 15-days free trial will full access to all features – you can start now and see your data coming into the platform in real time.

1.
Integrate your security data sources into the ThreatDefence cloud XDR platform in minutes—all data is hosted in Australia.
2.
Get your security controls assessment and report in real time, including Essential Eight maturity levels. Get immediate visibility into your on-premises systems, Office365 and AzureAD.

3.
Receive detailed onboarding training and ongoing training sessions for your IT team—your IT system administrators will become experienced security analysts over time.

4.
Receive a complimentary monthly meeting to get expert advice on your security posture, cyber risks, preventive technologies, etc.

5.
Receive detailed onboarding training and ongoing training sessions for your IT team—your IT system administrators will become experienced security analysts over time.

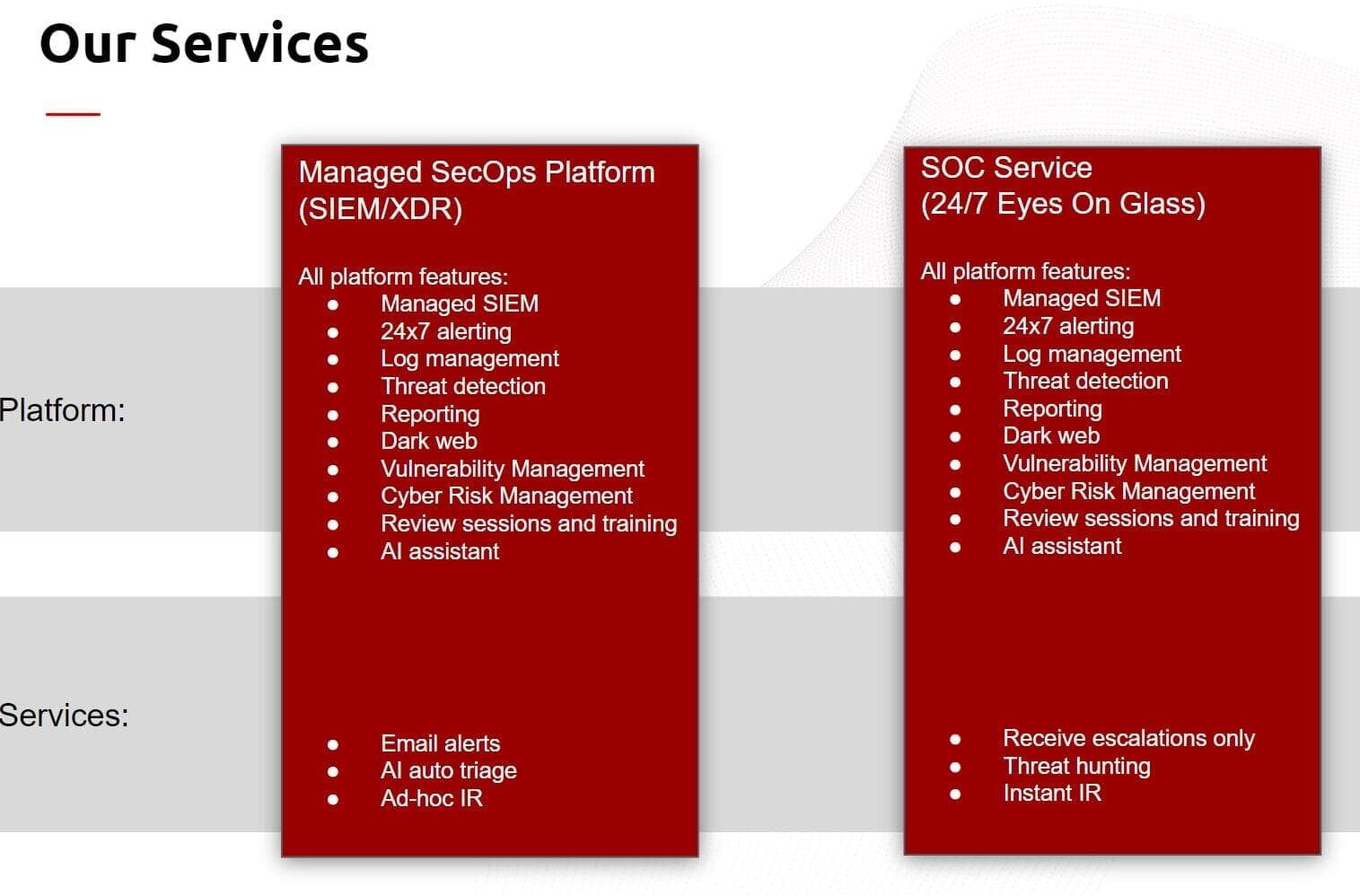
Solution Highlights_
ThreatDefence delivers continuous assurance across all your cyber security functions and enables your security operations with rich threat context and unbeatable visibility across endpoints, servers, cloud, and SaaS applications.
Paired with our 24×7 SOC as a Service, proactive Threat Hunting, and Incident Response services, ThreatDefence delivers unprecedented value to organisations of any size.
How we can assist_
The platform will provide valuable insights from day one, and was used on multiple occasions in government organisations to reveal:
- Compromised legacy workstations used by hackers on your network
- Compromised Office365 accounts
- Unexpected software
- Exposed and vulnerable systems
- Files with passwords in plain text stored by your users
- Insecure external connections
We become a part of your TEAM
Our XDR platform provides full enterprise coverage, integrating all the security data you can possibly reach into, including data that directly resides within your network and on your endpoints, as well as external data such as cloud workloads, SaaS applications, Dark Web breaches, compromised credentials, external vulnerabilities, and weaknesses and exposures related to third-party organisations in your supply chain.
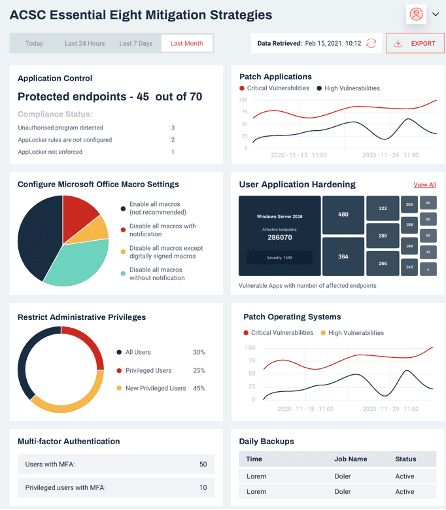
ACSC essential eight reporting
Our Customer Portal provides ongoing reporting, delivering a snapshot of your security posture in real time.
We have hundreds of security metrics in our platform, and we can report on any of them. Our reporting covers security posture overview, ongoing operational issues, security trends over time, as well as various compliance frameworks such as ISO27001 and ACSC Essential Eight.
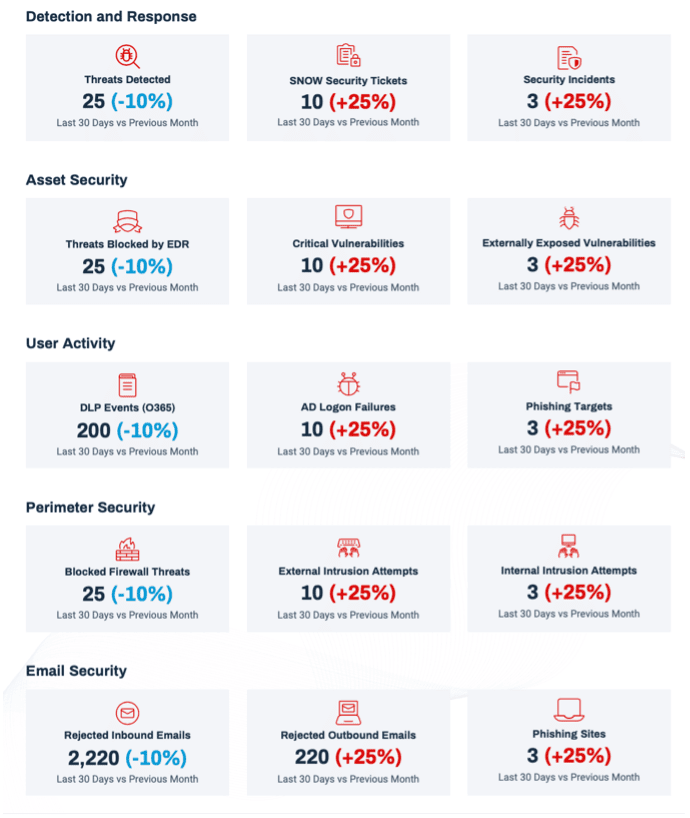
Business Case for your Cyber Detection and Response
Our platform provides an unmatched capability to visualise your networks and systems and expose high-risk areas across cloud, on-premises, or virtual and delivers an end-to-end cyber security solution, with full cycle detection, investigation, and response across all areas of your enterprise.
In addition to continuous, context-rich detection and response, our platform also brings a real-time security assurance capability to your organisation. It provides ongoing monitoring of security configurations on-premises and in cloud, as well as detection of vulnerabilities and weaknesses in your external perimeter and your partner organisations to give important context and help predict external threats before they get a chance to reach your environment.